Abusers in the WhatsApp realm
WhatsApp is a duo of trust & technology. This guide helps you understand the types of abuse over WhatsApp, how WhatsApp fights it, and how you can identify and avoid it.
I'm not affiliated with Meta or WhatsApp. The views and opinions expressed below are my own and do not reflect those of any company or organisation. I do not endorse, encourage, or support any method of tampering with, tweaking, or modifying any of WhatsApp's copyrighted material, products, or brand.
Introduction
Did you know that around 50% of all emails sent each day are spam? 162 billion spam emails worldwide, every day, out of 333 billion. Humans have been subjected to all forms of spam from as early as 19th century junk mail (or even earlier), to social messaging spam and many novel forms today. Spam comes paired with any communication channel humans use – WhatsApp included.
Spam is but one element under the umbrella of platform abuse. Any communication channel that reaches mass usage or has a significant population is subject to different kinds of abuse, for plenty of reasons. This is the equivalent of the eternal competition between armor and sword. Abuse tactics vs abuse prevention. I am confident that you know what abuse (e.g. spam, theft) looks like through phones, SMS, emails, social media, and social messaging apps.
Hell, I even came across a spam message from 1864 – a dentistry "advertising" their opening through a spammy telegram to a politician. Two words: mind blown.
If you’re building a business over WhatsApp today – whether you’re a product builder offering a service, a business owner using WhatsApp to run your operations, or an investor investing in a WhatsApp-based company – you need to clearly understand the risks of abuse on your business. Specifically, when it’s accidental and unknowing abuse. You need to know what you don't know that you don't know.
In a few short acts, I will take you through a tour of the sword vs armor in the communication realm – particularly within the kingdom of WhatsApp. You will understand:
What is platform abuse in WhatsApp and why you should care
Each of the forms of abuse, and how it affects your business, and finally
What to do to avoid it.
There will be entertainment and drama – this I can promise. Let's roll.
Act I: Sword & armor
A billion dollar question
100 billion messages & 100 million voice calls are sent over WhatsApp daily. I’m confident that spam on WhatsApp isn't as bad as email (for a variety of reasons). Looking at today's email spam rate, you can imagine the potential trend if abuse isn’t well fought on WhatsApp.
At the most fundamental level, WhatsApp's core benefit is staying connected with people who matter to me, and they matter most to me because I trust them the most. Trust is the bedrock of meaningful relationships, and these are the people we communicate most openly with.
I urge you to think about the following for a moment: Can you describe what WhatsApp fundamentally sells or offers, in one word?
WhatsApp sells trust. Not communication. Not connection. Certainly not an app. They sell trust. It is that you wake up every morning with enough trust that the most stable, convenient, secure, reliable, spam free, most *insert whatever* way to connect with those who matter to you is WhatsApp.
Most importantly, you trust that your important people are hanging out there, too.
I can bet you that the WhatsApp leadership folks wake up everyday thinking about how to protect their most important value proposition (p.s. I dislike the word value proposition to describe what's happening here – I call it the core job-to-be-done instead).
I look back at all the decisions WhatsApp made in their product over the years, and I see one clear pattern – the show must never stop, not even for a millisecond. Because if it stops, trust decreases rather quickly. All their decisions are around keeping the app running at all costs. Simplicity in product design, reduction in features compared to competitors, and a laser focus on getting a few core functions right instead of a hundred half-baked ones – these are all intentional decisions. These choices are to keep the app's purpose crystal clear; the app just works.
Want proof? A few years ago, false information was circulated about WhatsApp’s end-to-end encryption potency, leading flocks of people to move to Telegram and Signal. I mean, TELEGRAM! A messaging app on which you can literally build a custom client from scratch, sitting between you and their servers, and that can store every single message passing through – in plain text. It is a subpar channel compared to WhatsApp, but people didn't care at the time. They decided that WhatsApp broke their trust, and that any alternative, no matter how bad, was better than that.
The ways of abuse
I have a personal definition of abuse for messaging apps that’s simpler than most. Abuse is any activity that undermines WhatsApp user trust. That’s it. Yes, there can be intentional or unintentional abuse, but it’s still abuse. It still eats away the user's trust in the platform.
Abuse, and in particular spam, isn’t new to WhatsApp. Once a platform reaches mass usage or has a significant population, the abuse will appear, and consequently, the platform starts building defences. WhatsApp likely started taking spam seriously around 2013; maybe earlier. I expect that the 200 million active users mark is where they had some form of anti-spam effort dedicated to fighting abuse.
The abuser and the platform are in a continuous, constant fight of sword versus armor. As Matt Jones, who led the anti-spam engineering team at WhatsApp, eloquently put it in his talk:
... If it costs them 11 dollars just to make 10 dollars, they're not going to stick around for very long. So as we're trying to build detection mechanisms and new approaches, we have to think about this and say “how does this new approach make life more expensive for spammers?” ...
Abuse over WhatsApp happens in three different ways:
Security vulnerabilities
Reverse engineering
Exploiting logical gaps or poorly designed features
Most of the abuse comes through the reverse engineering approach. This is the act of breaking apart the components of a software (like WhatsApp), understanding how these components work together, and emulating or tampering with them to work in other ways for the benefit of the owner.
Sometimes, we reverse engineer software or hardware for non-malicious motives. I once had to reverse engineer the protocol of my digital camera to make it easier for me to transfer photos to my computer. Reverse engineering for convenience is real, and it happens. However, most of the time, reverse engineering opens the door to malicious motives, especially if the incentive is high enough.
This entire category of abuse is possible through what I label as 3rd party enablers. We will zoom in on 3rd party enablers for the rest of this article – who they are, why they exist, what they do, the harm they cause, and most importantly, how to detect and avoid them.
3rd party enablers
A 3rd party enabler is a non-official actor that modifies or replaces the official way of using WhatsApp for a certain benefit. Every single 3rd party enabler on the internet uses one or more types of reverse engineering approaches. Some are built purely for abuse, some for convenience, and some are just for fun. I will go through each method for both your entertainment and awareness.
One thing is certain: all of these methods eventually lead to conflict with the platform in various ways, which we will explore in Act II.
There are three main types of 3rd party enablers, each crazier than the other.
A full-fledged client (headless, or UI-based)
Back in 2018, I stumbled upon one of the first WhatsApp-API-as-a-Service providers, which was a reverse-engineered version of WhatsApp exposed as an API. I dabbled a little in WhatsApp Web myself, and it wasn't too hard to get something working, emulating the way WhatsApp worked, or exchanging a few messages. I contemplated whether or not I should build a business on this kind of API provider, but quickly realized that it would turn into a dark weapon for abuse, and wouldn’t be sustainable (and indeed, they shut down and came back up a few times).
Crazy as it sounds, WhatsApp was hit by a flood of fake clients some time ago (and some are still alive today). The likes of WhatsApp Plus, WhatsApp Blue, and many others. There is an official WhatsApp page dedicated to warning about unofficial apps. Actors who offer these clients reverse engineer how WhatsApp works (usually through the web), and build an app (usually an Android, iOS, or web app) that emulates all of its functionality. In doing so, they can offer extra functionality that's not possible through the official apps.
There is also the headless version, which is a piece of software that runs on a computer (usually a server), allowing all kinds of automations and abuse, such as bulk messaging, and more.
Usually, actors reverse engineer the way WhatsApp works by looking at how WhatsApp Web works. Even if there wasn’t a version of WhatsApp for the web, this wouldn’t stop bad actors – they’ll just do that with the standard apps instead.
An emulated client (virtual, or physical)
Because the above isn't crazy enough, here’s some more crazy soup for you. Some years ago, and probably still running now, there was what I call a virtual WhatsApp farm.
Imagine hundreds, if not thousands, of Android emulators running simultaneously on many servers in the cloud (or on-premises), choreographed to each run the WhatsApp Messenger (or Business app), and each with a registered virtual number of its own. The actors would warm them up for a few weeks, messaging each other and other numbers that aren't yet involved in malicious activities. They would use Residential VPN services to keep the IP addresses dynamic.
The goal of the warm up phase is to behave like any other standard WhatsApp user–adding a few connections, messaging, and so on. Then, they unleash the dirt, whether it’s a massive scam, personal info theft, advertising, or any other money-making scheme. A virtual, scalable abuse farm.
You get the point.
Yes, there’s also a version of this that’s a physical phone farm. Literally hundreds, if not thousands, of mobile phones behaving like I described above, except they’re physically accessible. I'll let you visualize the rest.
A browser extension
The last type is my arch enemy (not literally; I don't yet have a list of arch enemies, but when I do, I will write an article about them). Even though the types discussed earlier seem dangerous and destructive, this type is usually what brings harm to businesses, because it’s disguised as playing nice and as a convenient way to use WhatsApp for business. But in reality, it is the very opposite.
You know about WhatsApp Web, right? This type of enabler is a browser extension (for Chrome or Firefox) that runs on top of your WhatsApp Web. It usually helps you do things more efficiently, and makes WhatsApp even more convenient to use – often for business purposes. This sounds good and helpful, right? WRONG. This gets your account banned. But why? You might be tempted to think, “well, it doesn't sound fishy. It just compliments WhatsApp's functionality, and it runs in the same browser where I’m using WhatsApp Web. It’s just more convenient”. Again, wrong.
This type of browser extension has the ability to eavesdrop on everything you’re doing on WhatsApp. How? They have access to your browser tabs, including your WhatsApp Web tab. There is little or no way to add control or limit their access once you install the browser extension. Your media and your chats (both work and personal, incoming and outgoing) are like an open book. By sitting between you and WhatsApp's servers, these extensions can potentially access all your messages, contacts, and other sensitive information.
The core distinction between a browser extension and the official WhatsApp Business API is that a browser extension is uncontrollable. It doesn't have to operate within the rules. It also has access to way more information than official WhatsApp providers do (profile pictures, other private or non-work chats, etc.), and even access to other tabs if it wants to.
I’ve built two businesses over WhatsApp in the last 6 years or so, both on top of the WhatsApp Business Platform. I got to see my fair share of all kinds of eccentric WhatsApp setups. During these years, I spoke to thousands of customers using WhatsApp for their business every day. I collected data from 1760 customers and looked into the top reasons businesses face issues when using a 3rd party enabler. The majority of the account bans happened due to browser extensions. It became clear to me over the years that browser extensions, while not very sophisticated in their abuse or even malicious, can have the worst impact.
By the end of the next act, you will be an expert in the dos and don'ts of WhatsApp. You will be able to run a business reliably over WhatsApp without risk, make the right technology choices when building a business on top of WhatsApp, or know what you’re getting into before investing in a WhatsApp business that's destined to crash and burn.
Act II: Cost of abuse
This talk and WhatsApp's own whitepaper (titled “Stopping abuse: How WhatsApp fights bulk messaging and automated behavior” which you can find linked here) sheds some light on how WhatsApp fights spam.
Every month, over 2 million WhatsApp accounts are banned for bulk or automated behavior. Machine learning systems detect and ban suspicious accounts at registration, during messaging, and in response to user reports. WhatsApp analyzes account information, IP addresses, and carrier data to detect bulk registrations, and during messaging, WhatsApp monitors account activity patterns and behavior to identify automation and abuse.
Besides this, user feedback (reports & blocks) is used to evaluate accounts and improve detection systems. WhatsApp also limits group sizes and message forwarding to reduce the spread of bulk messages.
They analyze hundreds of factors to differentiate between normal and abusive behavior. Finally, WhatsApp works with providers to ban third-party apps that claim to offer unauthorized services for the platform.
Every time a 3rd party enabler modifies or tweaks or replaces the official way of using WhatsApp – the account is at risk of getting banned. This includes 3rd party browser extensions, and others.
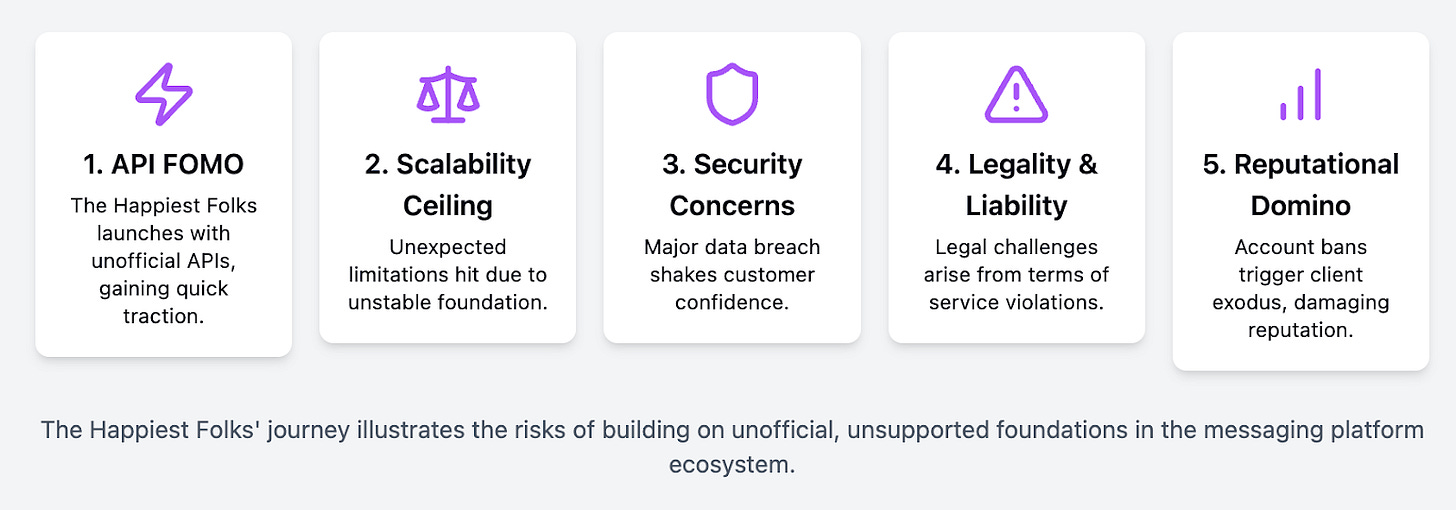
The Happiest Folks Inc.
The Happiest Folks Inc is a made-up business, but one that I have seen real life examples of over the years. They run their operations online, and WhatsApp cuts horizontally through their business, whether in sales, support, onboarding, success, or marketing.
At the start of their journey, being a tiny little company, they happily used the WhatsApp Business app, until they outgrew it. They needed to do more. They hired more people. They implemented a CRM. They wanted to measure performance. They wanted to automate. They started looking for ways to scale their operations over WhatsApp, and to deal with the high volume of conversations more efficiently.
Unfortunately, they chose what's seemingly convenient and cheap over what's reliable, scalable, and trustworthy. They asked their sales, support and success agents to install a browser extension (3rd party enabler) that works on top of their WhatsApp Web. The browser extension used unofficial APIs to get things done. It was convenient, but only in the short term. A few of their agents noticed that their accounts were getting banned, some of their automations stopped working, and their marketing team couldn't spin up campaigns over WhatsApp anymore. Some of their customers could no longer contact them.
A while later, their 3rd party enabler (the browser extension company) was hit by a security breach leaking all their customers’ personal information. They kept going. Eventually their 3rd party enabler was shut down due to a DMCA notice like this one. They were left out in the open and had a reputational crisis to deal with.
Their management understood that the way to go is to switch to the WhatsApp Business Platform – a wise decision that should’ve come sooner. Better late than never.
Legality & liability
I am not a lawyer, a legal expert, or have any background of this sort, but it’s not hard to decipher or understand where trouble is, and more importantly, how to avoid it.
It is clear cut in Meta's policy on the Unauthorized use of automated or bulk messaging on WhatsApp:
Any browser extension that enables abuse that violates WhatsApp’s Terms of Service, like automated or bulk messaging, is at risk. Notice that it is not just bulk messaging, but also any kind of automated messaging. A browser extension like the one below that can broadcast or automate messages on your behalf falls right within this category. I have seen countless instances of accounts getting banned because of this.
By using these tools, you are leaving it to others to decide, on your behalf, how to get around WhatsApp's own machine learning algorithms for detecting misbehavior or abuse.
DMCA
More than just violating WhatsApp’s terms of service, there is also the DMCA risk. This is a real life example of it in action, with content hosted on Github that causes harm to WhatsApp.
The DMCA (Digital Millennium Copyright Act) is a U.S. law that helps protect copyrighted works by allowing copyright holders to request the removal of infringing content from the internet. WhatsApp, whose software is protected by copyright and trademarks, found a few years ago that some developers had reverse-engineered its software and uploaded versions or tools related to it on GitHub. Examples include projects like WhatsAPI and node-whatsapp. To protect its intellectual property, WhatsApp sent a DMCA takedown notice to GitHub. After reviewing the request, GitHub agreed that the listed repositories were infringing on WhatsApp's rights and took them down.
WhatsApp used the DMCA to remove unauthorized projects from GitHub, safeguarding its software and trademarks.
The 3rd party enablers use technology that's built on these OSS (open-source solutions) reverse engineering attempts to grok how WhatsApp works, so you can imagine the impact on those companies. They will practically shut down the very next day after a DMCA takedown happens.
Reverse engineering
At the far end of the abuse spectrum, there is the infamous case of the government-backed NSO group for reverse engineering WhatsApp. Abuse can happen through malicious and secretive forms, and reverse engineering is at the root of the most sophisticated and coordinated methods. It is also the most expensive. There'd be at least a few teams working on spyware like Pegasus, and tens of millions of dollars spent on some of the hardest computer security problems to ever exist.
This may seem gibberish to non-technical people, but in short, the spyware contains multiple zero-day vulnerabilities against a particular version of iOS. The purpose is to override and install a man-in-the-middle spyware to intercept, record and transmit messages from messaging apps on the device, and forward it to the abuser's servers.
Orchestrating and stringing those vulnerabilities is extremely hard, but the consequences can be as big as bringing governments down, knowing how deeply penetrating and foundational some of the messaging apps on the market today are. Imagine by knowing someone's number, you can send them a link that gives you immediate access to their messages, calls and everything that's happening on the device. Sometimes the link doesn’t even need to be clicked.
The gist here is that any form of reverse engineering is going to be at least in the gray area, if not worse. It is simply not worth it to build a business or a product on top of a gray area – and especially if there’s a better route.
Reliability & high performance
There are different types of risks within the communication sphere, and any business owner has to think about ways to mitigate these risks. There are two primary risks that you need to consider: service disruption, and scalability limitations.
Service disruption: It is anything that compromises your ability to do business on a daily basis. If you’re using WhatsApp today, or your business is built on top of it, the most severe risk is the inability to use or communicate with customers over WhatsApp. A total service disruption.
This can happen if:
Your account is banned
Your provider (such as a 3rd party enabler) is unreliable
Your provider closes shop or faces legal issues
Scalability limitations: it is about outgrowing the current method of communication. Your business has scaled, but your method of communicating with your customers stopped scaling with your business. Worse, you can't replace the channel of communication because that's where your customers are. You’re stuck. You start to lose money because you’re dropping opportunities left and right.
This can lead to:
Inefficient operations
Missed opportunities (e.g. dropped leads, lost deals)
Poor customer experience
Reliability
A reliable messaging experience is one where sending or receiving messages just works. We take it for granted that if I send a message to my friend over WhatsApp today, it will be delivered. Tons of effort and time go into making this happen in the background. Tampering, tweaking, or replacing the behaviors of a product removes the guarantee that it will be a reliable messaging experience.
When you use 3rd party enablers (e.g. browser extensions or unofficial APIs), you face two core issues:
Account bans
Messages delivery issues
Account bans
Early in this act, we went through how WhatsApp analyzes hundreds of factors to differentiate between normal and abusive behavior. When you use a 3rd party enabler, you are under the mercy of how the 3rd party behaves or emulates WhatsApp's own behavior. Most don't do a good job at that.
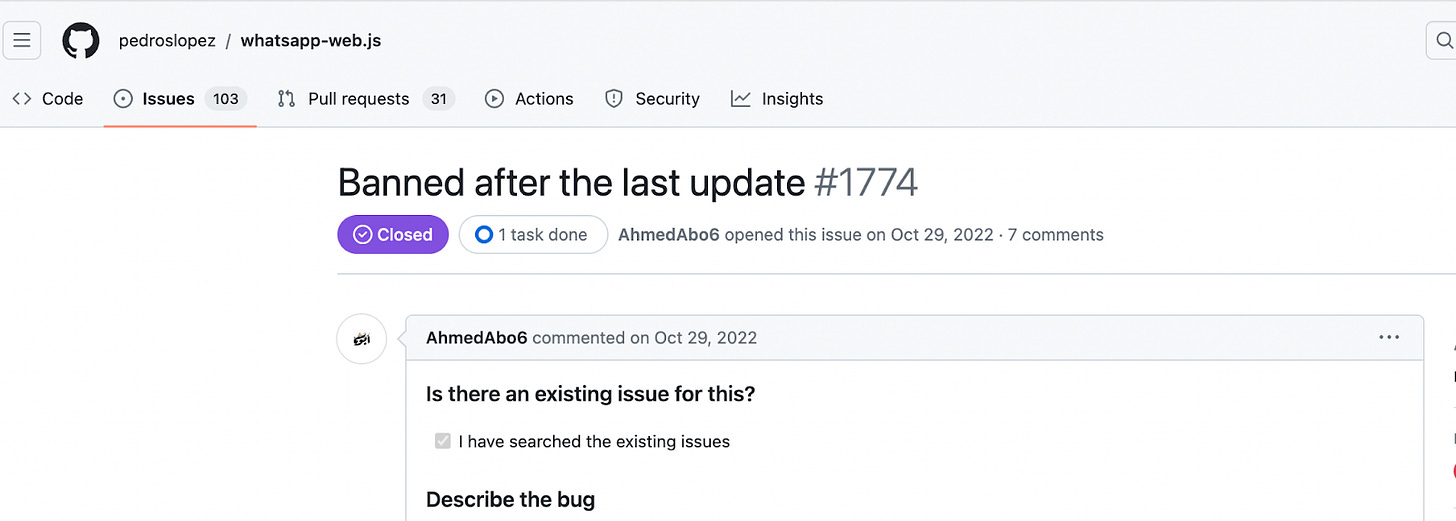
Any reverse engineered version of WhatsApp has one important goal: to simulate the way WhatsApp works in the closest fashion possible, so that it appears as a genuine client (WhatsApp Web, or the WhatsApp Messenger on iOS, Android, or any other desktop OS). If there is a slight misalignment on how they emulate the way WhatsApp clients work, WhatsApp will and can detect that through metadata analysis.
There are countless cases like the above, all over the internet, that detail this behavior. The case in this screenshot involves a GitHub issue in a reverse-engineered WhatsApp Web repository used by many third-party enablers. It is not that these types of solutions are malicious by intent, but it is a difficult and risky job to keep their versions in line with how WhatsApp works. Eventually, this risks accounts getting banned because these workarounds simply can’t keep up.
Message delivery issues
There are different types of 3rd party enablers as we covered earlier. Some assume complete control of the sending and receiving of messages, and sometimes all other operations within your WhatsApp experience. This is what we refer to as a full fledged client (headless, or UI-based). A browser extension might not necessarily do this.
What's important to know is that this type of 3rd party enabler would, in essence, emulate the functionality of your WhatsApp Messenger or WhatsApp Business app. You lose the guarantee of the messaging experience, because you hand it over to them.
You're effectively transferring your trust from WhatsApp's experienced engineering team to an unknown group of developers. WhatsApp's team has built and refined the messaging experience from the ground up. They understand every nuance of the system and are committed to its reliability. In contrast, 3rd party developers are reverse-engineering this complex system, often without full understanding or the resources to maintain it at the same level of reliability.
This directly impacts my trust in whether a message I send will actually ever reach my customers. Will I know if it never gets delivered? What do I do when it doesn't?
–
WhatsApp introduced their WhatsApp Business Platform (APIs) to offer businesses a reliable way to run their operations over WhatsApp as they scale. Long term commitment and reliable foundations are what you get using the official APIs. Meta has visibly put in significant effort and long-term organizational commitment around their WhatsApp Business Platform. Compare this with the unofficial APIs – if you are using a 3rd party enabler, you are likely just one step away from having a service disruption.
High performance
When your business is scaling, you want guarantees that your technology choices can scale with it. WhatsApp is a messaging service, so sending and receiving messages is core to the experience.
High performance in WhatsApp communication means:
Speed
High volume handling
Platform guarantees
Speed
Imagine you’re operating a B2C business selling baby strollers where parents would interact with you to ask questions about a certain stroller, and your messages, instead of arriving instantly, take a few seconds or a minute to arrive.
The parent has many questions about your product. It’s a back and forth conversation. There is a lot of interaction, including small touches of relationship building. You are, by the choice of technology (your 3rd party enabler), subject to receiving messages later than you should. You’d lose your prospect to a competitor who responds faster than you.
Plenty of issues like the above occur when trying to figure out a way to emulate how WhatsApp works. It is a never ending cycle of back & forth hacks, workarounds, tweaks just to get the basics to work (basics which are readily given and guaranteed by the official methods), all for what may be a small gain in convenience or functionality that a 3rd party enabler promises.
High volume & platform guarantees
Using a 3rd party enabler potentially risks one more guarantee when your messaging volumes start to ramp up. But why? Isn’t it just based on the existing WhatsApp products?
Any 3rd party enabler can modify, tweak, or replace the WhatsApp Messenger or Business app’s default behavior, which can intentionally or unintentionally affect the experience of sending and receiving messages.
Think of your messaging needs as powering a factory. The WhatsApp Business Platform is like the main power grid: stable and capable of handling high demands. 3rd party enablers are like rewired generators, they might work for small operations, but they're risky. These unofficial modifications could lead to sudden failures, similar to how 3rd party enablers might trigger account bans or be the cause of unreliable performance. The grid reliably delivers 1000 kilowatts, while the modified generators struggle past 100 and could fail unpredictably.
The WhatsApp Business Platform (API), as of today, allows you between 80 messages per second by default (4,800 per minute) and up to 1,000 messages per second (a staggering 60,000 messages per minute)! In this world, you’re unlikely to reach these limits.
You are guaranteed that the core messaging integrity is maintained, and you have a direct connection to the source system. No tampering, no tweaking, no replacements. It just works.
API FOMO
API fear-of-missing-out is real. The WhatsApp Business Platform (API) is like a fully functional remote control with infinite buttons. Giving up on using official APIs is like giving up this remote control for a 3-button analog controller with buttons that only work half the time. It’s unreliable, limited, and you miss out on many opportunities. More importantly, there’s no strong reason to make this compromise.
WhatsApp has three products in the market today: the WhatsApp Messenger, the WhatsApp Business app, and the WhatsApp Business Platform (API). Any 3rd party enabler (browser extension) runs their unofficial methods either on the WhatsApp Messenger or the WhatsApp Business app. Most new features or updates to the WhatsApp Business Platform (API) will likely never be available to you if you don't use the official APIs.
The WhatsApp Business Platform today has features that don't exist on the WhatsApp Messenger or WhatsApp Business app. Even more so, WhatsApp just announced that the WhatsApp Business Platform will offer Voice (or Business Calling) and Groups as an API, which are drastically different from the voice and groups features offered in the WhatsApp Messenger or Business app, as they are programmatic and open up an infinite set of possibilities and use cases.
You also miss out on higher customer engagement rates. How so? WhatsApp has introduced all kinds of interactive messaging components. Text is good in many cases, but it’s much easier to click a button, fill out a quick quiz, send a location, or select an item from a list. Every time the user has to make a choice when interacting with you, they’re going to choose the easiest option.
Using a browser extension or a 3rd party enabler takes that power away from you, and the experience away from your users. No 3rd party enabler today can allow you to send buttons, quick replies, lists, forms, or other types of engaging content over WhatsApp. CTAs work for a reason; they increase engagement, and eventually conversion.
Your business is going to be as successful as the investment you put in it, and a big part of this investment is technology. Any unofficial 3rd party enabler, like a browser extension, will always play the catch-up game with the official ways of using WhatsApp for business – a catch-up game of hacks and unreliable emulation.
Scalability ceiling
If you're starting to use WhatsApp for your business today, you can either use the WhatsApp Business app, or the WhatsApp Business Platform (API). A small business, like a flower shop that has 1 or 2 employees, would most likely go for the WhatsApp Business app, and it is the right choice. Larger businesses that run their sales and/or support operations over WhatsApp with tens or hundreds of employees interacting with customers are unlikely to go for the same choice as a small business.
But why? It’s simple. Their operational needs outgrew their customer engagement method.
Imagine a situation outside the context of WhatsApp. You are a small business, you have 1 sales person who uses their personal phone to call & respond to your group of 20 loyal customers. Things work out, you hire more sales folks, they follow the same method. You have a team of 5 salespeople, and all of a sudden, you start noticing gaps. You need to record your calls and review them with your team, coach and train those folks, set up IVR, assignment calls, and have voice mail recorded per salesperson. To achieve all this, you end up using a cloud phone system like Aircall.
You’ve outgrown the old way and need to scale up your processes and tooling.
Using a 3rd party enabler (e.g. a browser extension), which in turn is built on top of the WhatsApp personal business app, can help you scale to a limit. The more you grow, the closer you are to outgrowing your processes and tools.
Ask yourself the following questions:
Can we efficiently manage and track high volumes of customer conversations for multiple agents without compromising security or control?
Is there a way to integrate our WhatsApp communications with our CRM to eliminate manual data entry and ensure real-time data synchronization?
How can we implement a system for easy assignment, collaboration, and handover of leads or deals between team members and across functions?
Can we monitor and improve agent performance based on their WhatsApp interactions, and maintain accountability for lost leads or deals?
How can we ensure data ownership, continuity, and compliance with regulations as we scale our WhatsApp operations, especially when team members leave the company?
As your team grows, saving their time and letting automations kick-in is a big deal. I recently stumbled upon a team of around 50 sales people in a business. They all use their personal WhatsApp. At the end of each day, they spend 5 to 10 minutes per prospect taking screenshots of their WhatsApp conversations and uploading them to the CRM. Each person does this for about 10 prospects per day, up to 20 in some cases.
50 salespeople x 10 prospects x 5 minutes = A staggering 2,500 minutes, or 41 hours wasted EVERY SINGLE DAY.
This makes zero sense. It’s 100% automatable. 3rd party enablers or browser extensions built on top of WhatsApp try to automate this but fail miserably – they’re unreliable, and the risks are not worth it.
What's the answer? a well-built, reliable, two way sync using the WhatsApp Business Platform to cater for scale and automation.
Security
Imagine you're sending a private letter through a trusted mail service, but instead of a direct delivery, you hire a person who promises you not to open and read your letter before passing it along, and promises that the letter will be delivered. It is hard to trust just a promise. This is like a browser extension built over WhatsApp, potentially intercepting, and even storing a copy of your private messages, turning a trusted communication into one based on a promise.
You may be asking yourself, doesn’t every other provider, even the ones built on the WhatsApp Business Platform, offer more or less a similar promise?
I will elaborate on how and why these promises are radically different and come with completely different guarantees.
Tampering & modification
WhatsApp has built-in end-to-end encryption for all kinds of messages, media, calls, and other types of communications that happen over their apps or platform.
A method WhatsApp recommends is to use Code Verify to check if your current version of WhatsApp Web has been tampered with, modified, or has the end-to-end encryption guarantee broken. I always turn it on whenever I install a new browser extension that may affect my personal WhatsApp Web.
WhatsApp's own documentation warns and recommends against using any browser extensions to ensure the security of your messages.
Why?
Browser extensions can't avoid failing this verification test. Code Verify (an open-source tool) operates by comparing hashes: it checks the hash of WhatsApp Web's code against the hash generated when an extension is active. If the extension tampers even one bit with the current page’s code (which it must do to inject its own scripts, UI layer, etc), then Code Verify will signal a verification failure.
There’s almost certainly no way around it.
If you truly want to vet a browser extension, you need to research who created the extension, what their policies are and, just generally, whether they’re considered trustworthy. The effort spent on vetting a browser extension is an opportunity cost. This time and effort could be better spent on using the official WhatsApp Business API.
And for headless clients that completely replace your WhatsApp client’s experience, the tampering and modification risk is just not worth it. They have 100% control of what goes on. There is little to no visibility into the experience.
Opaqueness
When it comes to security, vetting a 3rd party enabler (whether a browser extension, or a headless unofficial client or API) is about visibility and evidence-based guarantees. The lack of guarantees of how the 3rd party enabler works creates a situation of opaqueness on how it operates, and whether it is trustworthy or not.
This vetting process can be complex, and most businesses are ill-equipped to handle it. While the source code may sometimes be publicly available (as with a browser extension), thoroughly inspecting and analyzing it requires significant technical expertise and time. Going through someone else's obfuscated code is a challenge, and worst of all, the code can be updated the day after your initial inspection, rendering your efforts useless.
Unlike the WhatsApp Business Platform, your vetting process for a 3rd party enabler (specifically a browser extension) starts with evaluating the vendor at the browser level. You are scrutinizing not just their systems but also their distribution method. A vendor building on top of the WhatsApp Business Platform will always work within the rules and boundaries of how the platform is designed to be used—what's possible within it, what's not, what's safe, what quality looks like, and so on. You won't have to worry about issues like malware being distributed as part of a browser extension that can leak or inspect data even beyond the WhatsApp Web experience. This is one of the many risks that exist with using a browser extension.
Another exercise: go through the top 10 WhatsApp browser extensions in the Chrome Web Store. How many of them have security compliance, like SOC or ISO? Credibility of the company or developer is another flavor of opaqueness. There is no easy proxy for you to trust the developers behind a 3rd party enabler you give access to your most trusted business-to-customer communication. At the end of the day, they have open access to your browser.
There are plenty of examples around potential damage, whether intentional or unintentional, that can happen. Unfortunately, this may have less to do with the 3rd party enabler and more with the inherent risk of browser extensions as a distribution method. Kaspersky's research illustrates how they found malicious browser extensions with more than 87 million downloads!
Finally, I’m not saying all 3rd party enablers are malicious—some aren't. Some have some form of compliance certification, such as SOC or ISO. The problem, even with compliance, is that it’s hard to discern what they can or can’t do, and ultimately, which ones are trustworthy, and which aren’t.
Act III: Armor
3rd party enablers = bans
The guts of the problem is that a 3rd party enabler modifying, tweaking, or replacing the WhatsApp Messenger or Business app can, intentionally or unintentionally, make your account appear suspicious in the eyes of Meta's systems, and therefore get you banned, forever.
That's what you want to avoid. That's why the WhatsApp Business Platform is the safest way to scale your business operations on WhatsApp. It has built-in mechanisms to prevent total and complete failure, whether in terms of quality or messaging reliability.
The formula
I’ve personally spoken to a few thousand customers over the years, and I’ve identified key elements that represent risk. I am a formula man. It works, most of the time, to quantify risk with numbers. At the very least, it gives you a framework to reason and think about risk.
So, I introduce you to the WhatsApp 3rd Party Enabler Risk Score. Let's call it WEPERS (W3PERS) from now on.
Like any scoring framework, this can be subjective, but we aim to establish reasonable thresholds of risk. This is not just about vetting 3rd party enablers, but also WhatsApp's official offerings, and even alternative messaging channels that may actually work better for you.
Run this scoring exercise on a 3rd party enabler (specifically, ones that offer a browser extension), and let me know what scores you get.
Each category is scored from 1-10, where 1 is lowest risk and 10 is highest risk.
Technical reliability risk (TR)
How often does this solution break due to WhatsApp updates? How quickly can it be fixed? Can it be fixed at all? If it can't, will this feature just stop working forever?
The more resilient the solution is to WhatsApp changes, the more reliable your business operations will be. You want to avoid solutions that frequently break or take days, weeks, or sometimes never get fixed after WhatsApp updates. Some updates risk disrupting the entire method.
An example of a high risk option here would be a browser extension built on top of WhatsApp Web that scrapes web elements for messages to sync them to other platforms. One small change in the HTML, and the extension’s job is over.
Some of the risks are:
Frequency of breakages due to WhatsApp updates
Developer's track record of timely fixes
Compatibility with different devices/browsers
Legal compliance risk (LC)
Does this solution comply with WhatsApp's Terms of Service? Does it risk account bans or legal action? Does it risk being shut down by DMCA notices and takedown processes?
The more compliant the solution is with WhatsApp's policies, the safer your business is. You want to stay away from solutions that operate in legal gray areas or violate WhatsApp's terms. Again, these can lead to account bans, legal troubles, and reputational damage that can be hard to recover from.
An example of an unsustainable option would be a browser extension like this that enables you to bulk WhatsApp your contacts. This goes directly against WhatsApp’s Terms of Service.
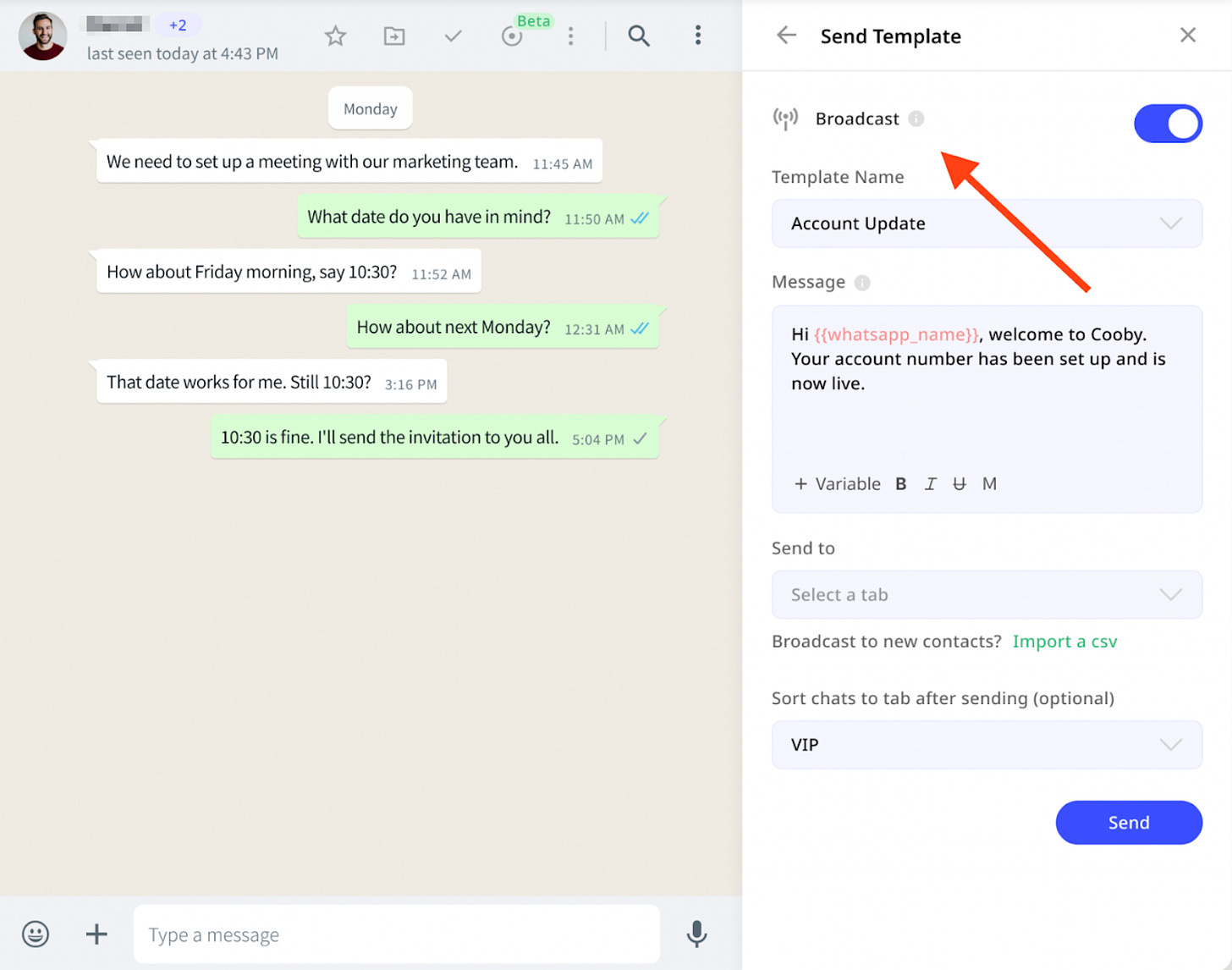
An example of a sustainable, legal, and safe option would be a browser extension built over the WhatsApp Business Platform to detect phone numbers on a certain web page, and allows you to send a template message to one or more contacts (assuming they’ve given their consent). Similar to the Aircall Dialer chrome extension, but one built over the WhatsApp Business Platform.
Some of the risks are:
Violation of WhatsApp's Terms of Service
Risk of account bans or legal action
Data handling and privacy concerns
Security vulnerability risk (SV)
How well does this solution protect sensitive business data and prevent unauthorized access? Does it sit between you and the customer? Do they have the right to sell your data, and your customer's? Do you trust the developer? Or is it a random browser extension built by an unknown developer?
The stronger the security measures, the better protected your business and customers will be. Avoid solutions that break encryption guarantees, have poor authentication, or are subject to known vulnerabilities.
Some of the risks are:
Exposure of sensitive business data
Potential for man-in-the-middle attacks
Authentication and encryption breakage or tampering
Feature parity risk (FP)
Does this solution offer all, some, or limited features of the official WhatsApp Business API? How will it handle future updates? Will it ever support engagement and interactive features?
The closer the feature set is to the official API, the more future-proof your operations will be. Most 3rd party enablers will score low here. You don't want to find yourself unable to use new, innovative features that your competitors can access while you’re stuck with unofficial wrappers.
An example of a high risk option would be one of the many OSS available that offer a headless, reverse engineered WhatsApp Web as an API.
Some of the risks are:
Missing official API features
Limitations compared to official solutions
Future feature compatibility
Business continuity risk (BC)
How easily can we migrate from this solution to the official API if needed? What's the impact on my business if this service suddenly stops?
The easier it is to migrate or have a backup plan, the more secure your business operations are. Avoid solutions that create high dependency or make it difficult to switch to official channels. You need to be prepared for the possibility that a third-party solution might become unavailable or unsuitable in the future.
Some of the risks are:
Dependence on the unofficial solution
Difficulty of migration to official solutions
Impact of sudden service discontinuation
Scalability risk (SC)
Can this solution handle our current messaging volume, grow with our pace, and integrate seamlessly with our other systems (e.g. CRMs, etc)?
The more scalable and integrable the solution, the better it can scale with you. Stay away from solutions that struggle under high volumes or don't play well with other business systems. For example, I’ve noticed over the years that using the WhatsApp Business app to manage a high volume of conversations daily can lead to an account ban.
Some of the risks are:
Performance under high message volumes
Ability to handle growing business needs
Integration with other business systems
Soup
A real life scenario I recently encountered with a business which, for fun, I ran WEPERS on.
For the sake of not naming names, I will call it Soup — a startup offering a browser extension for WhatsApp Web to enhance business communication for sales people. The extension offers features like automated responses, basic CRM integration like activity logging, broadcasts, and message scheduling.
Soup scores poorly on technical reliability due to inherent inability to respond to WhatsApp Web’s frequent updates. It also violates WhatsApp's Terms of Service by allowing broadcasts, which is a form of bulk messaging, meaning high legal risk. Security vulnerability is above normal; after all, it is a man-in-the-middle with weak encryption, or no encryption in some cases. Feature parity is low, lacking official API capabilities and interactive messaging support. Business continuity is at risk due to high dependence and difficult migration. Scalability is limited, struggling with high volumes and growing team needs – lastly, once there is a higher than normal volume on some of the salespeople’s accounts, that can trigger Meta's systems to flag suspicious activity, increasing the risk of account bans.
Technical Reliability Risk = 7
Legal Compliance Risk = 8
Security Vulnerability Risk = 9
Feature Parity Risk = 6
Business Continuity Risk = 7
Scalability Risk = 8
(7 x 0.2) + (8 x 0.2) + (9 x 0.2) + (6 x 0.15) + (7 x 0.15) + (8 x 0.1) = 7.55
This gets us a WEPERS score of 7.55!
Soup easily falls into the "Critical Risk" category. This is an example of a solution that you should avoid at all costs. It may work for a few days, or a few weeks, but it will most surely disrupt your business, and likely without any warning. This example is at the riskier end of the spectrum. There are many more that won’t score this high, but that doesn’t mean they don’t carry enough risk to stay away from.
But let me play the devil's advocate here. Even if Soup had a near-perfect Security Vulnerability risk score of 1, their total WEPERS score would still be a concerning 6.15. This highlights an important point: while security is critical, it's not the only factor. Legal compliance, technical reliability, and other risks remain significant.
So, even with bulletproof security, 3rd party enablers like Soup still pose substantial risks to your business.
When it comes to WhatsApp for business, official channels aren't just safer – they're often the only sensible choice.
Is it worth it?
As an observer, I think it is not in Meta's interest to see 3rd party enablers having a ball and eroding WhatsApp's trust.
But lately, I think Meta has been fighting back a little differently. They’re fighting back through delight. How? I’ve spoken about this in detail here. They are turning WhatsApp into a true platform, with capabilities that will make the benefits or conveniences of using a 3rd party enabler void and obsolete.
Every WhatsApp capability out there that makes the WhatsApp Messenger or Business app special will most likely be API-fied in the future. It will be scalable, customizable, configurable, and reliable—like a system of lego bricks that can be shaped into great products built on top of WhatsApp, benefiting millions of businesses. Evidence? The recent updates at the Meta conversations event in June included powerful platform announcements like Voice (or Business Calling), and Groups as an API.
I predict that in the next few years, we will see most, if not all, 3rd party enablers—specifically browser extensions—vanish. Eventually, businesses will see the true gold standard of using WhatsApp to scale through the WhatsApp Business Platform.
What does good look like?
Not all 3rd party enablers are bad or malicious. Although I recommend against using the majority of the 3rd party enablers out there, I think there is a version of what good looks like.
It’s a no-brainer that my first suggestion, for obvious reasons mentioned above, is to stick to the WhatsApp Business Platform. There are plenty of providers out there that do this well. It's their bread and butter.
Business use
Picking a provider built on top of the WhatsApp Business Platform is always a good start. But this doesn't mean you have to give up the convenience you found with 3rd party enablers.
For example, I’ve seen providers that built browser extensions over the WhatsApp Business Platform to detect phone numbers on a certain web page, and allow you to send messages to one or more contacts. Similar to the Aircall Dialer chrome extension, but one built for the WhatsApp Business Platform.
This type of browser extension acts as a helper or an assistant, rather than as an obscure layer that takes over and runs on top of your WhatsApp Web (which potentially breaks your end-to-end encryption, and other security guarantees).
You have clarity on what this browser extension does by inferring what is possible through the WhatsApp Business Platform. You also have several layers of protection against account bans, such as message template quality, phone number quality, account quality, and your Meta Business Account quality.
Moreover, you can be confident that this solution won’t suddenly break. It’s going to scale with you and your needs. It will allow you or your technical peers to extend and customize your WhatsApp interactions in endless shapes and forms.
Low risk, reliable, scalable, secure, convenient, and with endless customisation possibilities.
Conclusion
Phew, we covered a lot today. Most of what I wrote here has been sitting and building up in my head over a couple of years. It feels good to put it all together in one place.
To sum it up, here are the key takeaways:
WhatsApp is built on trust: it’s the backbone of meaningful communication, and abusing it, whether intentionally or unintentionally, erodes this foundational assumption.
Abuse is inevitable, but preventable: understand the risks, steer clear of 3rd party enablers, and prioritize business reliability, customer delight, and pick what’s future proof.
Official channels are the safest bet: the WhatsApp Business Platform is simply your safest bet for long-term reliability and sustainable operations.
The future is official and feature-rich: Meta is likely to continue expanding official capabilities, and highly likely that the unofficial methods will become obsolete.
Beware of short-term gains: quick fixes in the short term can lead to lasting damage in the future. Prioritize future-proofing your business.
This is the third article I’ve written about WhatsApp. I want to leave you with a personal note on why I write about this particular topic:
I’ve always found the idea of a message attractive and interesting. Any kind of message carries some form of intention. Whether we consciously choose or not, a message with an intention is a message with a motivation, and motivation is very human.
If I look back at the things that excited me the most in my career, it would be choices I made like working in my spare time on networking protocols (messaging between machines and people), or joining a business messaging company like Intercom, or building connections between messaging services (Slack + Intercom), or starting two companies in the business messaging space. How humans communicate with each other, and with other objects around them, and how this evolves is the most fascinating and exciting quest I can think of spending my time on.
Communication is never stagnant. It keeps evolving. It keeps changing. Today it’s WhatsApp, tomorrow it may be brain-to-brain LLM fine-tuned neural thinking protocol. I want to be part of it all and can't wait to witness how we evolve.
A huge thanks to my close friend Mohamed Elbadwihi for his feedback, copy editing, and relentless encouragement to get this done.


























I have to recognize this is one of the most complete breakdowns and reports on the whatsapp ecosystem, I'm building solutions based on the official WhatsApp API and this confirms that my decision on keeping this official (no third-party clients) was the best thing I could have done. Great article!
Wow, that is a detailed breakdown! It's clear email is not what it once was, due to abuse. I think WhatsApp has a great opportunity to embed itself into business communication workflows, by maintaining trust. But easier said than done, as your article points out!